If your network has any of the incorrect examples below, we will guarantee that operations will fail. Debugging network mis-configurations is time consuming and is not included in the reasonable price we charge for the software. We will offer advice to IT persons, when they request it.
The incorrect examples below are real mis-configurations we have found on customer networks.
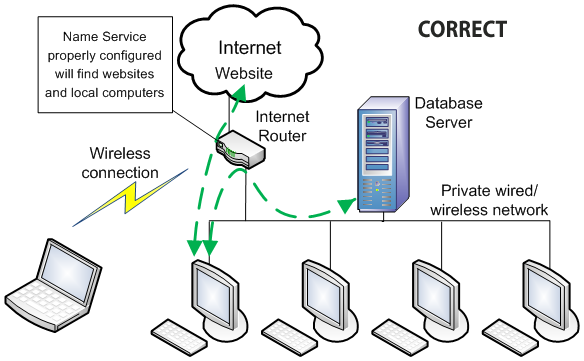
2. The computers on your network must be able to find the server computer with the database installed on it.
A Domain Name Service (or DNS) is like a phone book in that it contains a list of computers with their name and address. There are DNS services running all over the Internet. Internet based DNS services help you find websites. When you type the name of a website, the browser looks up the address of that site, then directs your request to that address. But DNS services running on the Internet do not know the addresses of computers on your internal network.
Computers on the same network can find each other by name.
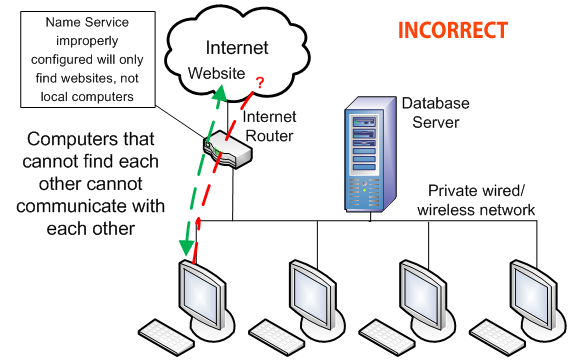
If your computers use an internet DNS service instead of one on your network, they'll only be able to find the addresses of websites, not a computer in the next room.
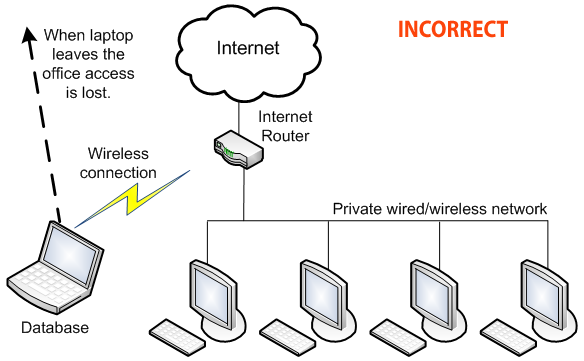
4. The server should not be a laptop or other computer that can leave the office unexpectedly. If this occurs your employees will no longer be able to connect to their data. If you want to access your data from outside your office, use the Cloud feature in the software.
Databases installed on laptops can leave the office unexpectedly preventing access to the data.
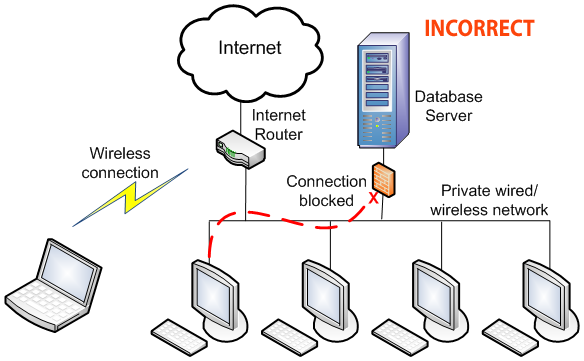
6. If you have a 3rd party firewall installed on your server or computers these must be configured to allow connections. The Database Manager automatically works with the Windows built-in firewall to correctly configure it, but not other security software.
A properly configured 3rd party security software will allow connections to and from software the administrator has specifically allowed. This requires someone trained in configuring it and is beyond what our tech support staff do.
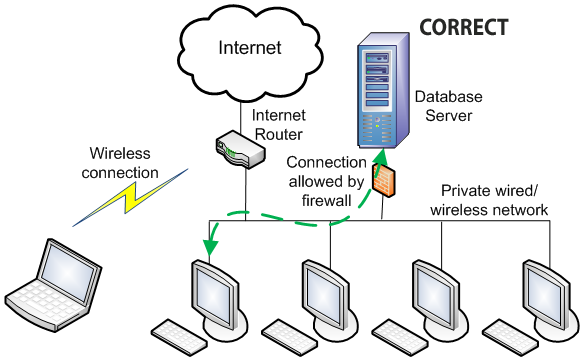
3rd party security software must be properly configured. If it isn't, connections can be blocked even when everything else is properly configured. If you have other security software or equipement installed on your network, you must have the IT Professional who installed it configure it. There are many 3rd party security products on the market and our tech support staff are not trained to configured them, so we will not attempt to do so. We can only refer you to the person who installed the equipment.